I am excited to share our Azure Security and Compliance Architecture for HIPAA/HITRUST – Health Data + AI + BI and API. We were awarded a non-equity investment grant by Microsoft's Startup team. We have built our whole platform on Microsoft’s Azure and launched our cloud-powered application in April of 2018. We selected MS Azure because it helps us comply with stringent regulations and standards for Health Data.
The best part of the Azure Security & Compliance PAAS is that it encompasses the exact Azure services architecture required to help CareRelay meet our HIPAA and HITRUST security, privacy, and compliance obligations, along with amazing support from the Microsoft consulting services and global support teams.
The solution is designed to consume consumer crowdsourced personal medical data and patient data using our own Fast Healthcare Interoperability Resources (FHIR), a worldwide standard for exchanging healthcare information electronically, and store it in a secure manner. Our partners can then use our Azure Machine Learning Studio deployment to take advantage of powerful business intelligence tools and analytics. The goal is to improve patient outcomes after discharge (PODS) from hospitals or outpatient management handling scheduling and compliance of the patient's care plan.
By engaging the patient's self-care and/or the family caregivers with the integrated data to keep the care team informed and on top of the care plan. Reduce caregiver and patient stress improve outcomes with notifications for actions and follow up for missed items.
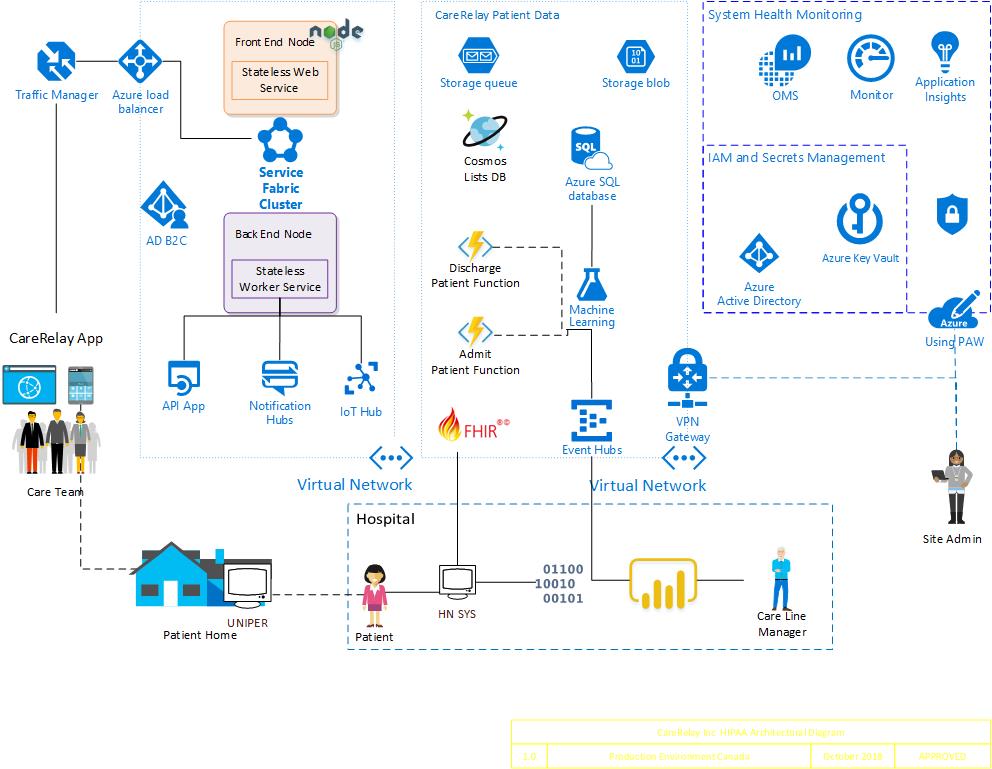
Architectural diagram. The diagram shows the reference architecture used for the blueprint to build CareRelay and integrate with services partners, hospital facilities and distribution partners.
Solution components
The foundational architecture is composed of the following components:
- Threat model A comprehensive threat model is provided in a tm7 format for use with the Microsoft Threat Modeling Tool, showing the components of the solution, the data flow between them, and the trust boundaries.
- Health review. The solution was reviewed by Coalfire Systems, Inc. for The Health Compliance (HIPAA, and HITRUST).
The Health Insurance Portability and Accountability Act (HIPAA) is a US healthcare law that establishes
requirements for the use, disclosure, and safeguarding of individually identifiable health information.
It applies to covered
entities—doctors’ offices, hospitals, health insurers, and other healthcare companies—with access to
patients’ protected health information (PHI), as well as to business associates, such as cloud service
and IT providers, that
process PHI on their behalf. (Most covered entities do not carry out functions such as claims or data
processing on their own; they rely on business associates to do so.)
The law regulates the use and dissemination of PHI in four general areas:
- Privacy, which covers patient confidentiality.
- Security, which deals with the protection of information, including physical, technological, and administrative safeguards.
- Identifiers, which are the types of information that cannot be released if collected for research purposes.
- Codes for electronic transmission of data in healthcare-related transactions, including eligibility and insurance claims and payments.
The scope of HIPAA was extended with the enactment of the Health Information Technology for Economic and Clinical Health (HITECH) Act. Together, HIPAA and HITECH Act rules include:
- The HIPAA Privacy Rule, which focuses on the right of individuals to control the use of their personal information, and covers the confidentiality of PHI, limiting its use and disclosure.
- The HIPAA Security Rule, which sets the standards for administrative, technical, and physical safeguards to protect electronic PHI from unauthorized access, use, and disclosure. It also includes such organizational requirements as Business Associate Agreements (BAAs).
The HITECH Breach Notification Final Rule, which requires giving notice to individuals and the government when a breach of unsecured PHI.